 |
ELAG - Enterprise Systems |
| Home | Framework | Products | Samples | Contact |
This section will outline all the generic functionality in ELAG applications. Entire subsystems as modular building blocks are explained under 'Samples'
Claims Management System, main screen, first tab:
Fig 1. A typical ELAG screen ELAG screens can open as many times as necessary. In other words, you may view 3 different data sets in 3 copies of the same screen at the same time. Screens have a master list. Master list columns (and combinations) sort ascending or descending. List columns can be changed on the fly at anytime (by ELAG staff). The buttons labelled A-G on the right change the column set for the particular data set being viewed, so that large data sets can be sub-grouped comfortably. Screens have an Export tool, with which to export master list data.Screens have fields, or child lists, or both, editable or read only depending on requirement, whose contents relate to the row highlighted in the master list. These can be arranged directly on the screen, or in tabs. Editing a row in the master will lock that row out to all other users while the change takes place. Buttons are either graphical checkboxes (two-state values with descriptive English for both cases), or momentary 'Action Buttons', meaning that by pressing the button a process - usually a business rule or special output - is triggered, and, optionally, logged. Screens have selection criteria fields, which determine what data appears in the master list. Selection text boxes use standard asterisk wildcards, and will take any number of phrases up to 256-512 characters (depending on requirement). Phrases to be searched for are delimited by semicolons. Text fields can also implement 'fuzzy' searches - which will yield several parts of speech (phone: phoned,phoning). Screens allow Font and Font Size selection. saved preferences available but not recommended except in mission-critical output pipelines (mass doc generation, mass shipping, billing etc.). Note fields (unlimited text) can be freeform (any text can be edited with appropriate permission), audit-trailed (entering a note tags it with your name, time, and date, after which the note is no longer editable), or automated (user picks from a list of frequent phrases, thereby not needing to type and standardizing the sentence). See below.
Fig. 2 An Audit-trailed note tool
All lists have HTML Report Export Function - with layout preferences. Other formats in all lists:
Reports can be custom-made but with user-defined, dynamic elements, including:
Database roles are simply a way for a database to group users. A user can have many roles (groups), and a role can be within another role. ELAG provides: Database
Role-based, row-level SQL Select security (you only see items you are allowed to). For Internet deployment, Citrix (gotomypc.com) is the most secure distribution method available, since only a rastered, incremental bitmap appears outside the firewall.ODBC/JDBC data pipes stay within the company firewall. Web development IS available, of course.
Row-level,
audited edit locking even within multiple instances of a screen
in the same application.
The first
ELAG executable is distributed to all client workstations
by an Installshield package. An email to employees distributes
a link to the package. Included is a loader program which
updates executables from a central machine as new versions
become available. Subsequent executables just get delivered
alone (under 1 MB, maximum 2) and handled by the same loader program.
This is one of the features that make continuous rapid prototyping
possible.
ELAG can translate to the following with little change: Spanish Swedish, Danish, Norwegian, Finnish Multiple
currency management - transactions or receivables - available
on request
Modules, depending on complexity of customization and size, can be delivered from 2 to 8 weeks from order approval.
ELAG
has sets of programming and naming standards for Data Modelling
and Procedure Writing. These are enforced by code generation
tools, since they output repeated code, but mostly with sheer
discipline, oversight and QC. The overriding concept, easily
explained in plain English, is that all database tables, fields,
view and procedure names are exceptionally long and descriptive,
and are named after the very business concepts they model
- so much so that if a button is labelled 'Confirm All Invoices
Have Printed', chances are the database procedure it triggers
is ConfirmAllInvoicesHavePrinted. As straightforward
as this may sound, it is the exception, not the rule in the
software business. The end result is that when client questions
arise, ELAG's technical representative speaks the client's
language by design, because the database he is looking at
is self-documenting.
|
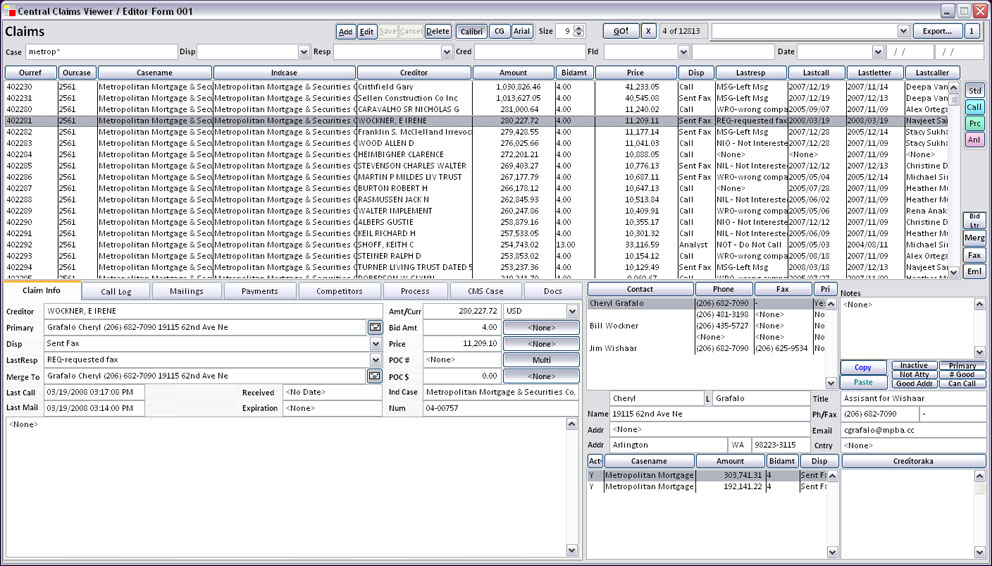
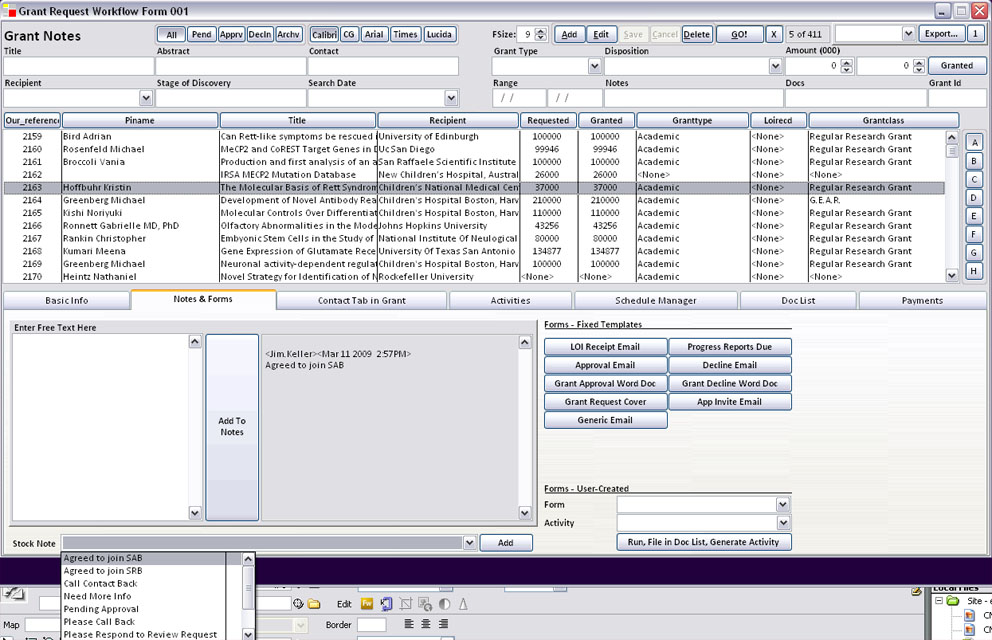
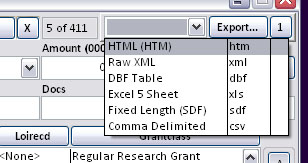 Fig.3 The Export Tool
Fig.3 The Export Tool